In this first of a six-part series, we will introduce the NIST-CSF and its functions, categories, and subcategories. The CSF Core is grouped into of five functions:
- Identify
- Protect
- Detect
- Respond
- Recover
These functions represent a basic risk management approach, where risks are related to specific threats, vulnerabilities, and consequences. There is a clear chronological order to the process, starting with identifying assets and risks, and ending with recovering from a potential breach. As we will see later, some categories are nonetheless overlapping and even redundant (which is not necessarily a bad thing in risk management.)
Each function has several categories and subcategories, although not nearly evenly distributed:
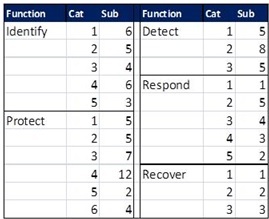
The “Identify” function has five categories and a total of 24 subcategories, the “Protect” function has six categories 35 subcategories, the “Detect” function has three categories and 18 subcategories, the “Respond” function has five categories and 15 subcategories, and the “Recover” function has three categories and only 6 subcategories. The number of subcategories under each category varies widely too, from 1 to 12.
This imbalance is both a result of the consensus-oriented development process that is open to all stakeholders and interested parties, as well as an emphasis on preventing disruptions rather than recovering from it. The first is laudable, but the latter is lamentable.
Data breaches are so common these days that they really should be considered inevitable. They may not always be as costly or widely-publicized as the Target or OPM breaches, but the fact that even these big organizations with large cybersecurity divisions are breached demonstrates that even the best prevention needs to be accompanied by robust response and recovery. Unfortunately, these two functions receive by far the least attention, with only 15 and 6 subcategories, respectively.
In the next part of this series, we will describe each function in detail, and provide some examples of real-world cases and applications, and how novaturient can help organizations achieve their security goals.
