Note: This is the combined version of our six-part series published earlier, plus a new conclusion.
Background
The National Institute of Standards and Technology’s Cyber Security Framework, NIST-CSF, is a broad-based initiative to increase the security posture of organizations of all sectors and sizes. While some may be familiar with the venerable NIST SP 800 series of computer security publications, the new framework incorporates this and other standards as reference for a less technical and more organizational approach to information security within a company. It is expected that the NIST-CSF will become a recommended application and best practice in many sectors, and might be part of future contractual requirements for companies doing business with the federal government, or a prerequisite for insurance benefits.
Our novaturient experts are actively engaged in the NIST-CSF development process via public notices and meetings, and have taken a closer look at the current version. In the following article, we will introduce the CSF and its functions, categories, and subcategories.
Overview
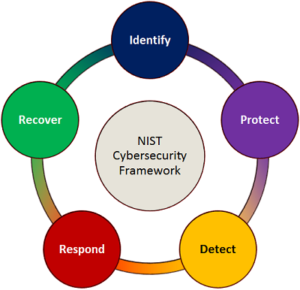
The CSF Core is grouped into of five functions:
- Identify
- Protect
- Detect
- Respond
- Recover
These functions represent a basic risk management approach, where risks are related to specific threats, vulnerabilities, and consequences. There is a clear chronological order to the process, starting with identifying assets and risks, and ending with recovering from a potential breach. As we will see later, some categories are nonetheless overlapping and even redundant (which is not necessarily a bad thing in risk management.)
Each function has several categories and subcategories, although not nearly evenly distributed:
The “Identify” function has five categories and a total of 24 subcategories, the “Protect” function has six categories 35 subcategories, the “Detect” function has three categories and 18 subcategories, the “Respond” function has five categories and 15 subcategories, and the “Recover” function has three categories and only 6 subcategories. The number of subcategories under each category varies widely too, from 1 to 12. This imbalance is both a result of the consensus-oriented development process that is open to all stakeholders and interested parties, as well as an emphasis on preventing disruptions rather than recovering from it. The first is laudable, but the latter is lamentable.
Data breaches are so common these days that they really should be considered inevitable. They may not always be as costly or widely-publicized as the Target or OPM breaches, but the fact that even these big organizations with large cybersecurity divisions are breached demonstrates that even the best prevention needs to be accompanied by robust response and recovery. Unfortunately, these two functions receive by far the least attention, with only 15 and 6 subcategories, respectively.
In the next five parts, we will describe each function in detail, and provide some examples of real-world cases and applications, and how novaturient can help organizations achieve their security goals.
CSF Core Function One: Identify
Asset Management. Business Environment. Governance. Risk Assessment. Risk Management Strategy. These are the five categories in this function. Sound familiar? Of course! This is the bread and butter of any strategic planning and management within an organization. The tools used to assist in that process are often part of the Enterprise Risk Management (ERM) function, and reflect industry-wide standards and regulations, such as COSO, COBIT, SOX, or ISO 27001. How is this related to cybersecurity? Simple! In a hyper-connected world, cybersecurity is not a separate function isolated in the IT Department, but an integral part of everyday activity and thus, everyone’s responsibility.
Maintaining clear roles and responsibilities in regards to risk is indeed the main goal behind the activities described in the 5 categories and 24 subcategories. The activities themselves are rather straightforward: Identifying, determining, inventorying, mapping, documenting of assets, systems, networks, and policies. This is a necessary step towards the goal, but not sufficient. The more difficult task: Understanding internal and external dependencies, and communicating the insights. It is here where organizational maturity and knowledge management are arguably at least as important as IT expertise. Our staff at novaturient can provide both, to help companies successfully identify their roles, responsibilities, and risk.
CSF Core Function Two: Protect
With 6 categories and 35 subcategories, it is by far the most expansive function within the framework, for better or worse. This reflects the traditional view that cybersecurity, and security in general, is first and foremost a matter of preventing bad things from happening – it is no coincidence that the motto of many police departments is “Protect and Serve.” “Protect the Server” might as well be the respective motto for traditional cybersecurity – it is the activity companies spend the most time and money on, be it through built-in features, or add-on protection using specialized software. Employees are instructed to use strong passwords and secure their equipment, and warned not to fall for phishing scams that could open the door for hackers.
Five of the six categories – Access Control, Awareness and Training, Data Security, Maintenance, and Protective Technology – describe these and related activities. Typically, the IT Department has either the lead or a primary supporting role in suggesting and implementing products and processes in this space. Yet, this may not be the optimal organizational solution. In the “Protect and Serve” analogy: IT Departments are in fact not Police Departments, and cybersecurity goes beyond “Protect the Server.”
A more comprehensive approach to the protection function is exemplified in the remaining category, Information Protection Processes and Procedures (IP), which is not only the largest in terms of subcategories, but also the most constructive from an organizational point of view. It promotes security policies that address purpose, scope, roles, responsibilities, management commitment, and coordination among organizational entities, as well as processes, and procedures that are maintained and used to manage protection of information systems and assets. The subcategories are applicable across the enterprise, and adopt a view of risk as a combination of threats, vulnerability, and consequences.
One might argue that this category is too wide-ranging to be implemented effectively, and only someone at the C-level would have the authority to reach into all these different parts of the organization, it is precisely that enterprise-wide understanding that moves cybersecurity from “Protect the Server” to “Secure the Organization.” We at novaturient can assist in finding the right organizational form to move towards that goal.
CSF Core Function Three: Detect
The three categories in this function – Anomalies and Events, Security Continuous Monitoring, Detection Processes – are somewhat aligned with the three categories that comprise risk as defined in the guiding risk management standards: Threat, Vulnerability, and Consequence. Anomaly detection is used to understand attack targets and methods, in other words: sift through the noise of the massive data volumes a system has to deal with every second. This is also part of the traditional data assurance task. Security monitoring of the physical, cyber, and human components of an enterprise system is the equivalent of mitigation vulnerabilities. It is introspective in that the main focus is looking at the organization and its systems and assets independently of external threats.
The advantage of giving priority to internal security is that the organization actually controls those systems and assets and should be very familiar with their (good or poor) performance. Strengthening internal security is far easier, and cheaper, than trying to predict or prevent any and all external threats. To use a common analogy: You cannot prevent another vehicle from hitting your car, but you can at least wear a seatbelt. We at novaturient specialize in organizational performance and change management, and analyzing companies’ strengths and weaknesses.
CSF Core Function Four: Respond
What happens when something happens? Who you gonna call? Answering these questions is the essence of the four categories and 15 subcategories of this function. During and immediately after a disruptive event, be it a fairly routine outage or an extreme breach, there needs to be planning, communications, analysis, and mitigation of the problem. It is the sitrep stage of cybersecurity, where reports and analyses are conducted based on the evolving situation. Sometimes, this stage can feel chaotic, with uncertainty and ambiguity of the exact scale and scope of the situation, compounded by miscommunication and misinterpretation. To counteract such problems, an integrated and iterative planning, testing, and training program should be instituted. While there are certainly costs associated with such programs – mostly in terms of employee time and attention – they are uniquely suited to become more and more efficient and effective over time. Why? Because IT and cybersecurity problems are a daily reality in modern organizations, and while it may sound counterintuitive, failures and errors are in fact hallmarks of so-called High-Reliability Organizations (HRT). In such organizations, mistakes are seen as opportunities to learn and improve, rather than as occasion to assign blame. The idea is to encourage individual responsibility without fear of retribution, thus making everyone a part of the response team.
We at novaturient specialize in performance and change management, and preparing companies for constructively dealing with the organizational side of both routine outages (high probability / low impact) and extreme events (low probability / high impact).
CSF Core Function Five: Recover
With three categories and six sub-categories, this is by far the shortest and least-detailed function of the Framework. And even the three categories are really only two distinctive ones, planning and communications, since the improvements category relates entirely to the planning process. In other functions, improvement is in fact only a subcategory, not a category.
It is a rather puzzling that so little attention was paid to this function. Size doesn’t always matter; but in this case, the brevity is a major flaw and ignores two facts: One, the very real possibility that even smaller-scale disruptions can threaten the very survival of a business if not handled properly. The common example in the physical realm are fire and other disasters – over 25% of businesses that experience such damage don’t survive. Two, the increasing frequency of failures or breaches (see part five) that make cyber incident response, and thus recovery, an almost routine event. Paying only cursory attention to recovery programs that go beyond “putting out the fire” creates new risks to the organization.
For our clients, novaturient suggests using enhanced recovery categories that are more in line with the rest of the framework, and, more importantly, enable them to continuously operate in the face of cyber and other disruptions. Specifically, we add a Business Continuity and Resilience category and three subcategories to the lineup, and modify several other subcategories:
Conclusion
As with all standards and frameworks, the NIST-CSF in and of itself is not perfect. Its value-added is through application and customization within the enterprise. The biggest strength is its seamless integration with other established industry standards – it does not try to reinvent the wheel and will save companies’ time and money by building on existing processes. The biggest weakness is its rather cursory treatment of recovery operations – it focuses attention and resources on protective measures, which are undoubtedly important. However, as FBI Director Mueller stated in 2012: “There are only two types of companies: those that have been hacked, and those that will be.” In other words, breaches are a virtual certainty, and dealing with the resulting losses of data, time, money, customers, and reputation needs to be a priority.
The NIST-CSF will continue to develop, and it is expected to become a recommended application and best practice in many sectors. In addition, it might be part of future contractual requirements for companies doing business with the federal government, as well as a prerequisite for insurance benefits. To stay ahead of the curve, let novaturient help your company implement the NIST-CSF, and confidently deal with the organizational side of both routine outages and more severe cybersecurity events.
